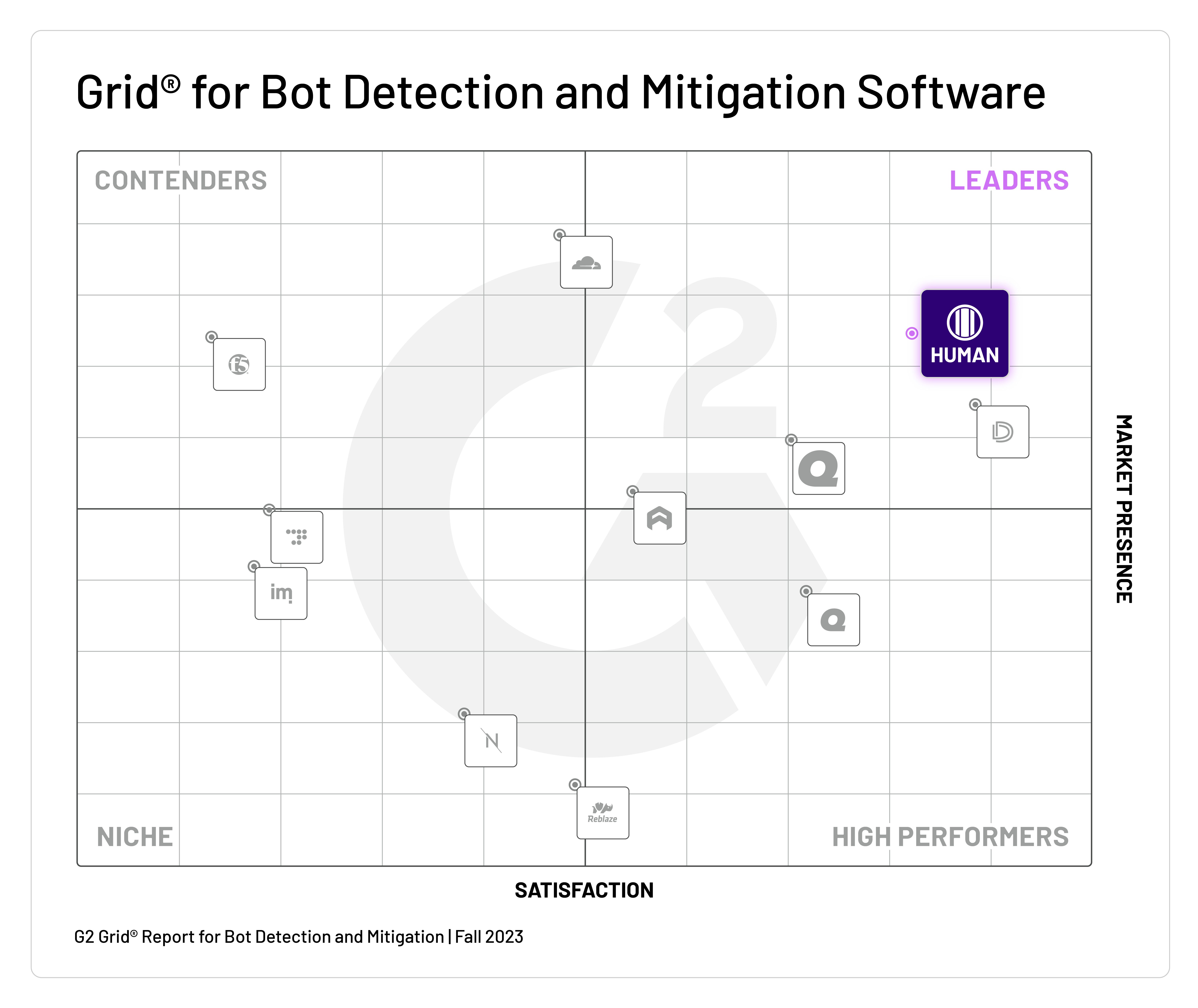
-
Platform
-
-
Human Defense Platform
One powerful platform to safeguard your entire organization from digital attacks
-
Account Takeover
Prevent account compromise
-
Account Fraud
Detect fake account creation
-
Transaction Abuse
Stop fraudulent financial transactions
-
Scraping
Block unwanted data exfiltration
-
Client-Side
Avoid client-side attacks and PII leakage
-
PCI DSS Compliance
Satisfy PCI DSS 4.0 requirements
-
Data Contamination
Ensure accurate data and analytics
-
Programmatic Ad Fraud
Protect digital advertising transactions
-
Malvertising
Serve clean ads
-
Human Defense Platform
-
-
Holiday Readiness Guide: Stop Fraud in its Tracks
 EbookHUMAN Security on Google Cloud will help you stave off those holiday bot blues.August 21, 2023
EbookHUMAN Security on Google Cloud will help you stave off those holiday bot blues.August 21, 2023 -
2023 Bad Bot Holiday Report
 ReportGrinch bots, carding, and account abuse during the holiday season.August 9, 2023
ReportGrinch bots, carding, and account abuse during the holiday season.August 9, 2023 -
A CISO’s Guide to Fraud Prevention: The Art of Modern Defense in Online Fraud
 EbookBy incorporating modern cybersecurity defenses and emphasizing proactive strategies, CISOs can more effectively safeguard their organizations.July 11, 2023
EbookBy incorporating modern cybersecurity defenses and emphasizing proactive strategies, CISOs can more effectively safeguard their organizations.July 11, 2023
-
Holiday Readiness Guide: Stop Fraud in its Tracks
-
-
Products
-
-
Request a Free Bot Risk Assessment
Learn More
-
Request a Free Bot Risk Assessment
-
-
HUMAN Bot Defender
Protect web and mobile applications and APIs from sophisticated bot attacks
-
HUMAN Bot Defender
-
-
Account Defender
Safeguard online accounts from fraud and abuse
-
Account Defender
-
-
Code Defender
Protect your website from client-side supply chain attacks
-
Code Defender
-
-
Credential Intelligence
Stop real-world credential stuffing attacks with an additional layer of defense
-
Credential Intelligence
-
-
BotGuard for Growth Marketing
Protection for your marketing funnel and sales efforts
-
BotGuard for Growth Marketing
-
-
MediaGuard
Protection for DSPs, SSPs, media owners and brands from fraud
-
MediaGuard
-
-
cleanAD
Protect against malvertising
-
cleanAD
-
-
For Security
Minimize vulnerabilities and defend your organization from advanced threats
-
For Fraud
Prevent business loss and keep your customer’s experience friction-free
-
For Ad Tech
Protect advertising supply chains and digital channel investments to boost ROI
-
For Marketing
Improve your performance marketing by keeping fraudulent traffic out of your digital channels
-
For Product
Preserve digital experiences that are free of fraud and abuse for real humans
-
For Security
-
-
Learn
-
-
Blog
HUMAN Insight and Research from our team
-
Case Studies
See what customers have to say about HUMAN
-
Webinars
Videos and content about HUMAN expertise and industry intelligence
-
Blog
-
-
Resource Center
Blogs, whitepapers, research, videos, articles—all in one place
-
Documentation
Details about HUMAN's products and interfaces.
-
Resource Center
-
-
Satori Threat Intelligence Research Team
HUMAN’s Satori Threat Intelligence and Research Team proactively uncovers and disrupts bot-driven threats.
-
Bot Insights
Get the insights you need to protect your business from bots
-
Satori Threat Intelligence Research Team
-
-
Company
-
-
Leadership
Meet the elite bot threat hunters dedicated to making the internet a safer place
-
Board of Directors
Meet the minds behind HUMAN’s mission
-
The Human Collective
Collective protection to fight ad-based fraud
-
Leadership
-
-
Satori Threat Intelligence Research Team
HUMAN’S Satori Threat Intelligence and Research Team proactively uncover and disrupt bot-driven threats
-
Satori Threat Intelligence Research Team
-
-
Human Overview
 How does HUMAN protect the internet from the influences of sophisticated bots? Read more in our overview.Download
How does HUMAN protect the internet from the influences of sophisticated bots? Read more in our overview.Download
-
Human Overview
-
Partners
-
-
The Human Collective
Collective protection to fight ad-based fraud
-
Partnerships and Integrations
HUMAN integrates with several technology partners, ensuring bot mitigation success in any environment.
-
Resellers
Explore HUMAN's technology through channel partners, combining bot mitigation and other security solutions.
-
The Human Collective
-
-
Become a Partner
HUMAN collaborates with the world's leading technology companies
-
Partner Portal
Log into the HUMAN Partner Portal for collateral, documentation, and other partnership needs.
-
Become a Partner
-
- Request a Free Bot Risk Assessment
- Request a Demo
-
Platform
-
-
Human Defense Platform
One powerful platform to safeguard your entire organization from digital attacks
-
Account Takeover
Prevent account compromise
-
Account Fraud
Detect fake account creation
-
Transaction Abuse
Stop fraudulent financial transactions
-
Scraping
Block unwanted data exfiltration
-
Client-Side
Avoid client-side attacks and PII leakage
-
PCI DSS Compliance
Satisfy PCI DSS 4.0 requirements
-
Data Contamination
Ensure accurate data and analytics
-
Programmatic Ad Fraud
Protect digital advertising transactions
-
Malvertising
Serve clean ads
-
Human Defense Platform
-
-
Holiday Readiness Guide: Stop Fraud in its Tracks
 EbookHUMAN Security on Google Cloud will help you stave off those holiday bot blues.August 21, 2023
EbookHUMAN Security on Google Cloud will help you stave off those holiday bot blues.August 21, 2023 -
2023 Bad Bot Holiday Report
 ReportGrinch bots, carding, and account abuse during the holiday season.August 9, 2023
ReportGrinch bots, carding, and account abuse during the holiday season.August 9, 2023 -
A CISO’s Guide to Fraud Prevention: The Art of Modern Defense in Online Fraud
 EbookBy incorporating modern cybersecurity defenses and emphasizing proactive strategies, CISOs can more effectively safeguard their organizations.July 11, 2023
EbookBy incorporating modern cybersecurity defenses and emphasizing proactive strategies, CISOs can more effectively safeguard their organizations.July 11, 2023
-
Holiday Readiness Guide: Stop Fraud in its Tracks
-
-
Products
-
-
Request a Free Bot Risk Assessment
Learn More
-
Request a Free Bot Risk Assessment
-
-
HUMAN Bot Defender
Protect web and mobile applications and APIs from sophisticated bot attacks
-
HUMAN Bot Defender
-
-
Account Defender
Safeguard online accounts from fraud and abuse
-
Account Defender
-
-
Code Defender
Protect your website from client-side supply chain attacks
-
Code Defender
-
-
Credential Intelligence
Stop real-world credential stuffing attacks with an additional layer of defense
-
Credential Intelligence
-
-
BotGuard for Growth Marketing
Protection for your marketing funnel and sales efforts
-
BotGuard for Growth Marketing
-
-
MediaGuard
Protection for DSPs, SSPs, media owners and brands from fraud
-
MediaGuard
-
-
cleanAD
Protect against malvertising
-
cleanAD
-
-
For Security
Minimize vulnerabilities and defend your organization from advanced threats
-
For Fraud
Prevent business loss and keep your customer’s experience friction-free
-
For Ad Tech
Protect advertising supply chains and digital channel investments to boost ROI
-
For Marketing
Improve your performance marketing by keeping fraudulent traffic out of your digital channels
-
For Product
Preserve digital experiences that are free of fraud and abuse for real humans
-
For Security
-
-
Learn
-
-
Blog
HUMAN Insight and Research from our team
-
Case Studies
See what customers have to say about HUMAN
-
Webinars
Videos and content about HUMAN expertise and industry intelligence
-
Blog
-
-
Resource Center
Blogs, whitepapers, research, videos, articles—all in one place
-
Documentation
Details about HUMAN's products and interfaces.
-
Resource Center
-
-
Satori Threat Intelligence Research Team
HUMAN’s Satori Threat Intelligence and Research Team proactively uncovers and disrupts bot-driven threats.
-
Bot Insights
Get the insights you need to protect your business from bots
-
Satori Threat Intelligence Research Team
-
-
Company
-
-
Leadership
Meet the elite bot threat hunters dedicated to making the internet a safer place
-
Board of Directors
Meet the minds behind HUMAN’s mission
-
The Human Collective
Collective protection to fight ad-based fraud
-
Leadership
-
-
Satori Threat Intelligence Research Team
HUMAN’S Satori Threat Intelligence and Research Team proactively uncover and disrupt bot-driven threats
-
Satori Threat Intelligence Research Team
-
-
Human Overview
 How does HUMAN protect the internet from the influences of sophisticated bots? Read more in our overview.Download
How does HUMAN protect the internet from the influences of sophisticated bots? Read more in our overview.Download
-
Human Overview
-
Partners
-
-
The Human Collective
Collective protection to fight ad-based fraud
-
Partnerships and Integrations
HUMAN integrates with several technology partners, ensuring bot mitigation success in any environment.
-
Resellers
Explore HUMAN's technology through channel partners, combining bot mitigation and other security solutions.
-
The Human Collective
-
-
Become a Partner
HUMAN collaborates with the world's leading technology companies
-
Partner Portal
Log into the HUMAN Partner Portal for collateral, documentation, and other partnership needs.
-
Become a Partner
-
- Request a Free Bot Risk Assessment
- Request a Demo

/HUMAN-Network-Effect@2x.png?width=781&height=588&name=HUMAN-Network-Effect@2x.png)